Report: Understanding disaster resiliency factors for broadband deployments
Executive summary
With the ongoing implementation of the $42.45 billion Broadband Equity, Access, and Deployment (BEAD) program, all levels of the public sector are currently working with private companies, nonprofits, and cooperatives across the country to meaningfully close our broadband infrastructure gaps.
By statute, states and territories will first target the unserved areas (with less than 25/3 Mbps) for new deployments, and these deployments will most often use fiber-to-the-home technology, which is considered the most “future-proof” telecommunications infrastructure. This is because of fiber’s ability to easily scale to accommodate faster and faster bandwidth needs, and the fiber cables themselves are likely to have a useful life of 30-40 years or more if installed correctly.
Building infrastructure that is intended to last that long, however, introduces a host of challenges and uncertainties, especially considering the evolving frequency and severity of natural disasters.
The importance of accounting for natural disasters
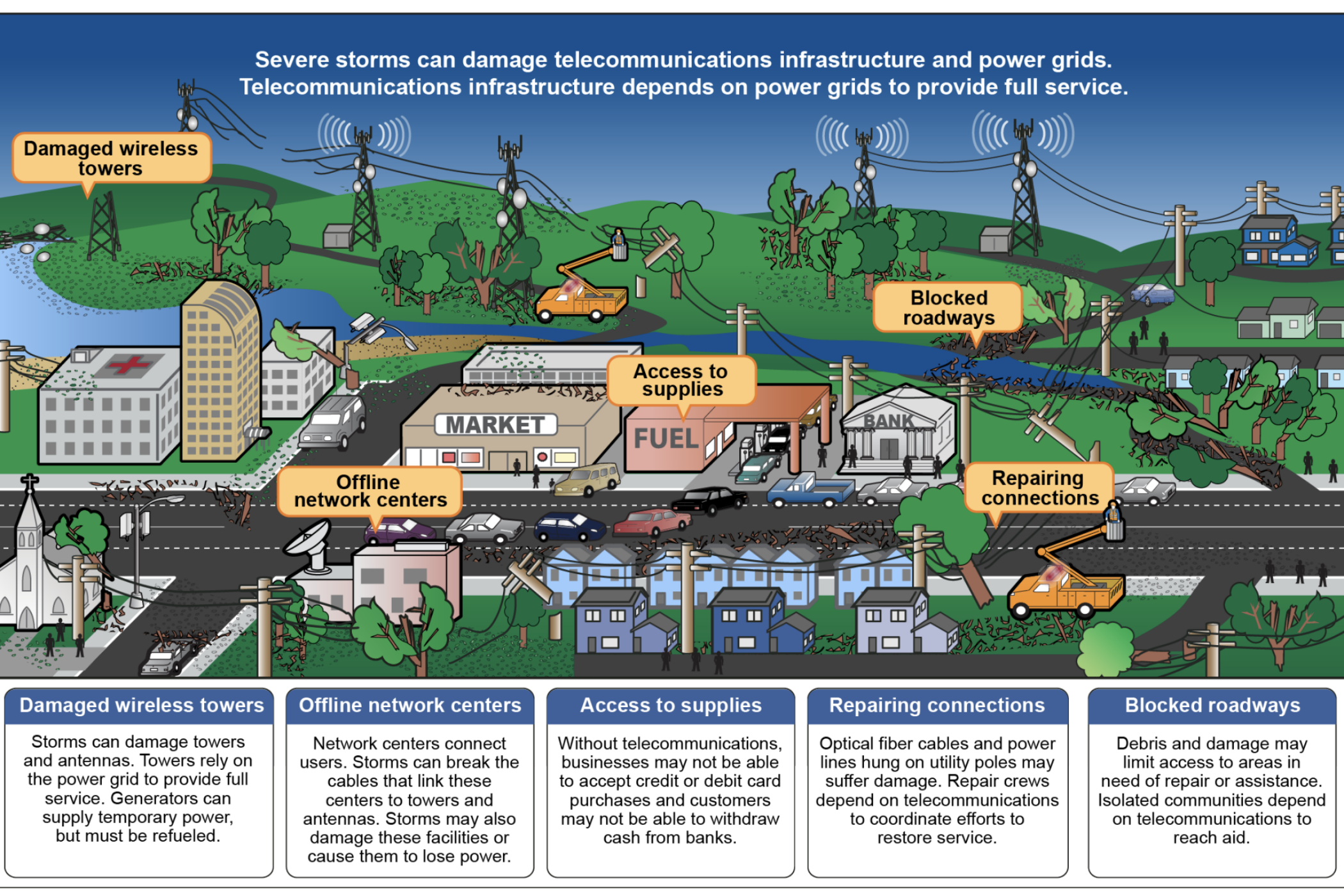
Natural disasters can severely damage broadband infrastructure, causing network failures that interrupt the continuity of many dependent commercial, governmental, and social activities. Importantly, recent notable disasters have led to multi-day —or longer — outages of internet and mobile broadband, which have severely hampered immediate rescue efforts, the coordination of recovery work, and even the ability for governments to issue text- and phone-based evacuation orders.
The BEAD program, as outlined in the Infrastructure Investment and Jobs Act (IIJA), requires that states and territories, as well as the ultimate funding recipients, take into account climate-related disasters in BEAD-funded deployments.
However, the IIJA does not offer significant guidance on how to do so. This report, and the accompanying Broadband Climate Risk Mitigation Tool, are intended to help policymakers understand how to encourage deployment of broadband networks that are more resilient to natural disasters.
Recognizing that every region in the United States encounters infrastructure risks associated with natural dangers, the tool associates broadband access and anticipated BEAD deployment areas with Federal Emergency Management Agency’s (FEMA) National Risk Index, a foundational risk appraisal tool, at the census block level. Further, this report contains research that illuminates the breadth of vulnerability in the continental U.S., and widespread relevance of taking resiliency into account when deploying telecommunications infrastructure.
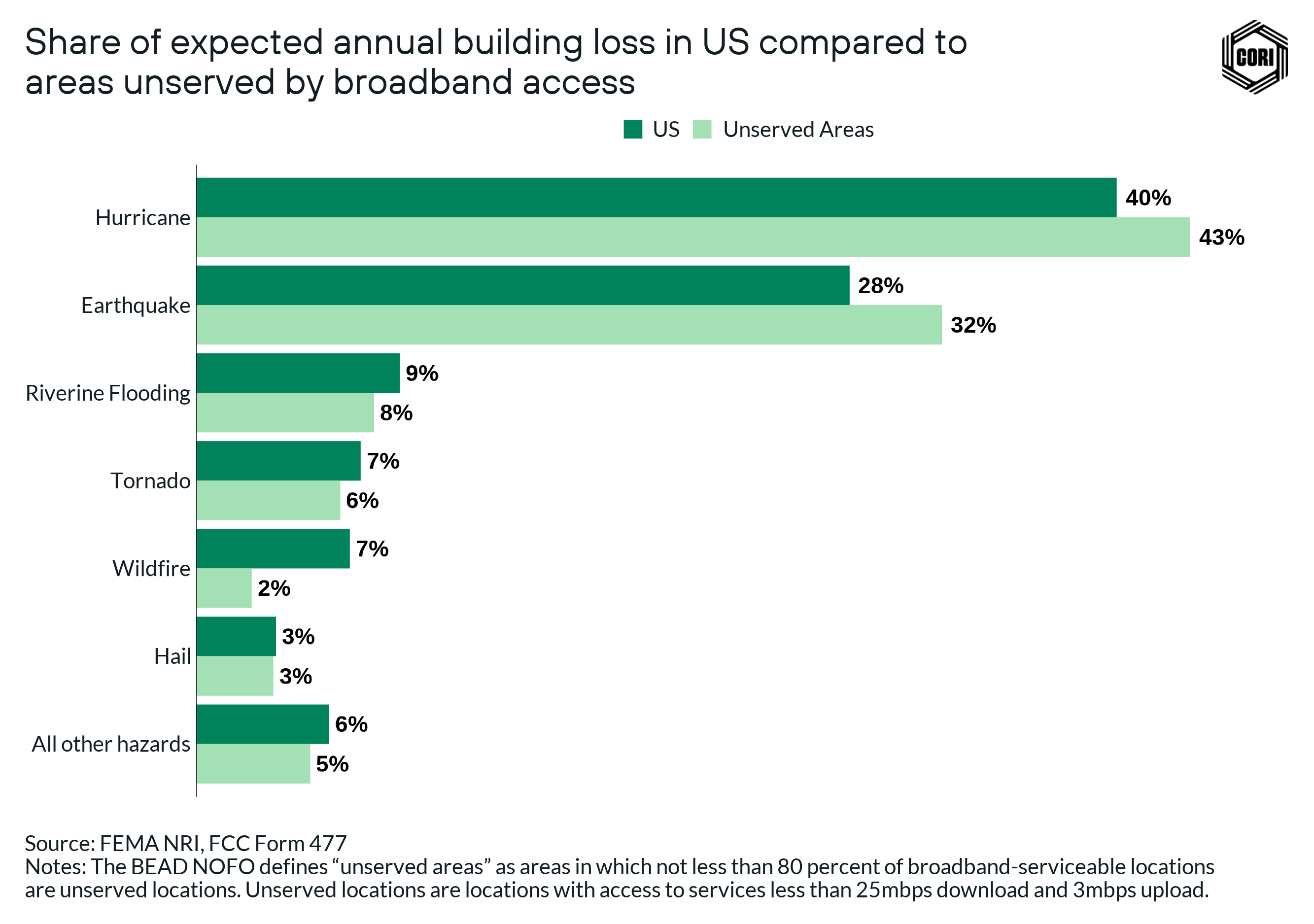
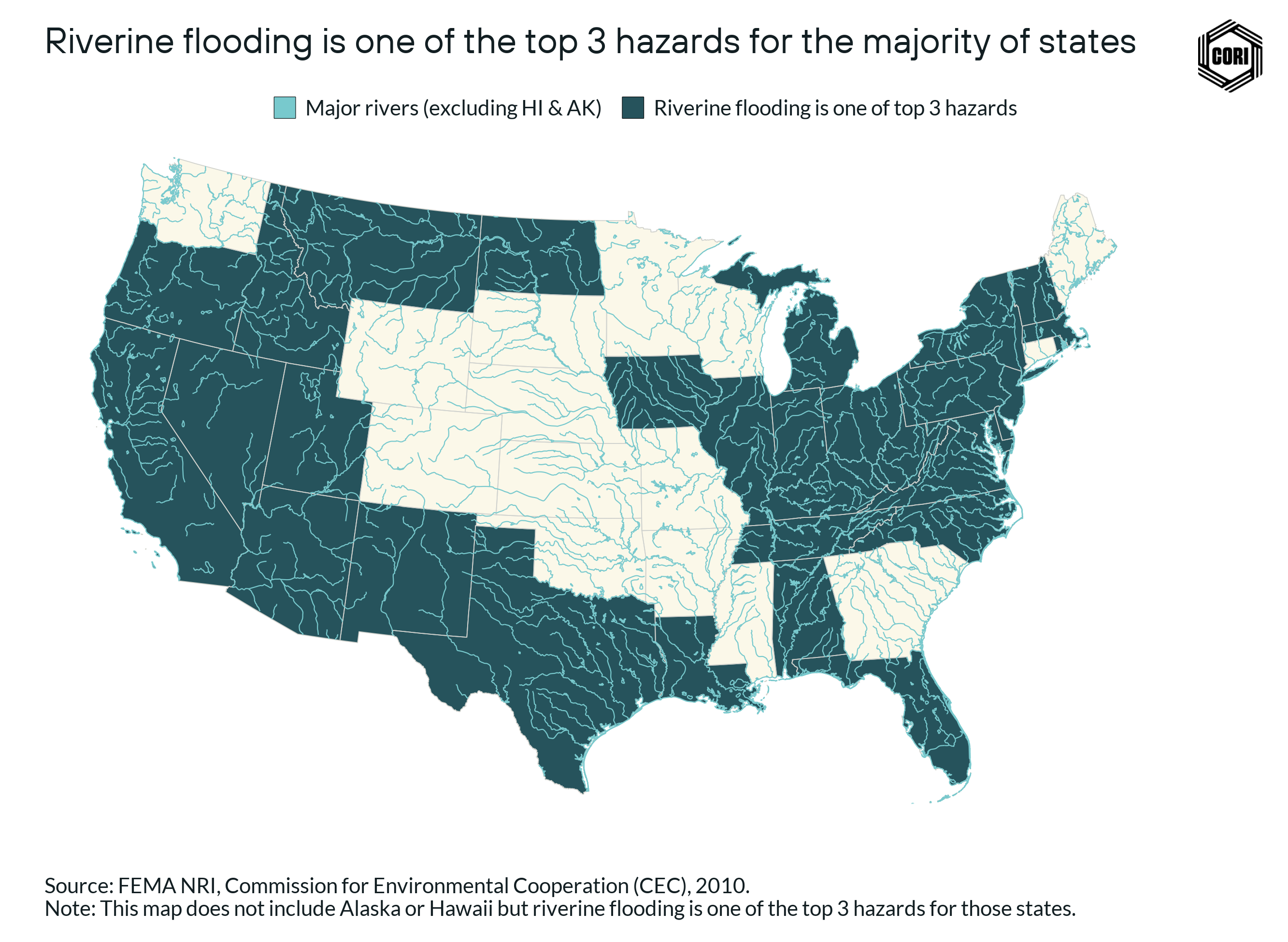
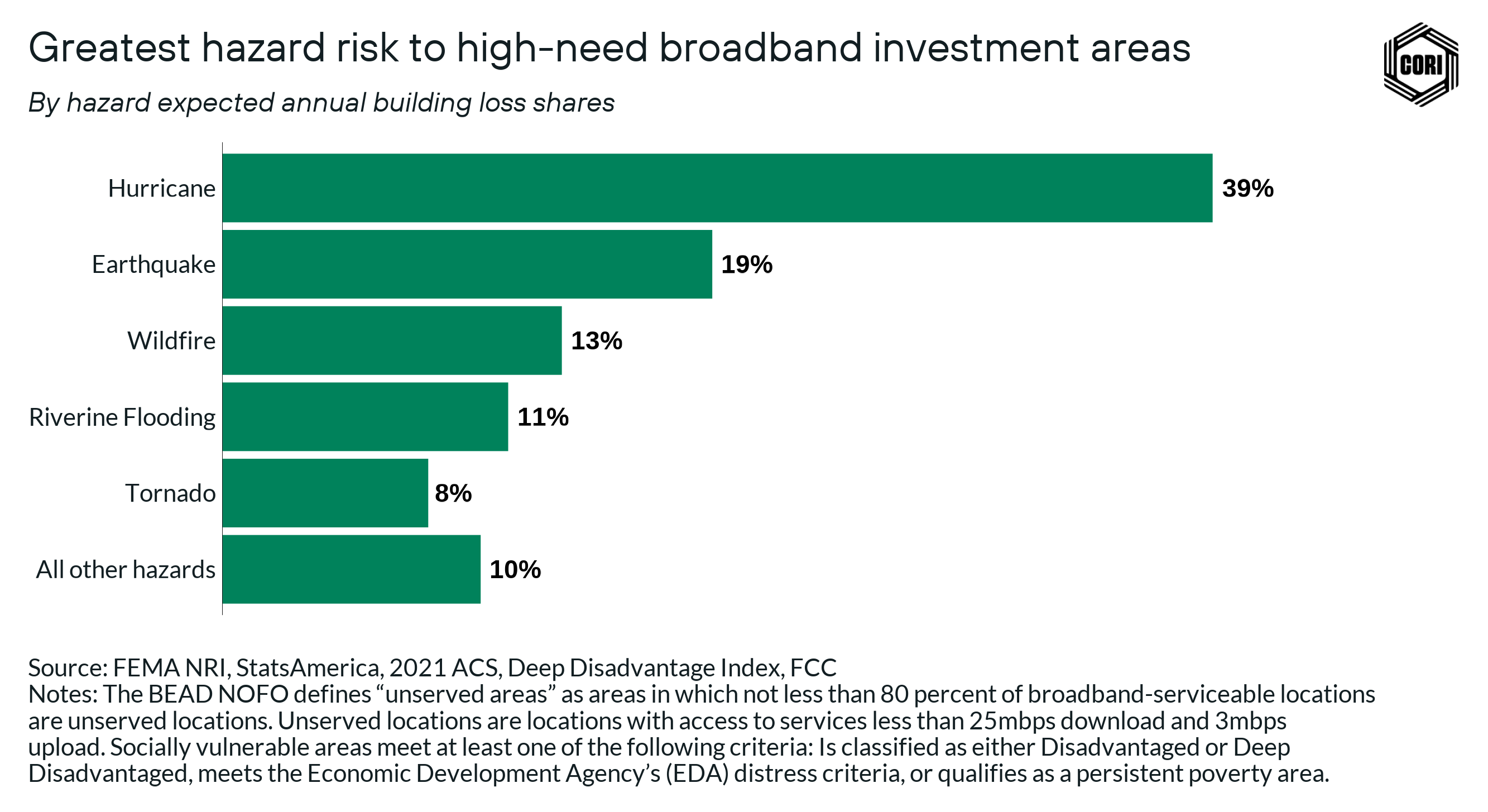
For example, this analysis makes clear that in certain areas of the country, such as hurricane-prone areas in the Southeast, there are a greater percentage of unserved census blocks that are much more vulnerable than the nation as a whole. Hurricanes are likely to cause the most destruction in unserved locations across the country in the aggregate (accounting for 40% of total anticipated destruction), however, the most common hazard across the largest number of states is riverine flooding.
Factors to consider
In Appendix A, this report offers a list of disaster impacts on broadband deployments, as well as possible mitigation efforts, and highlights some fundamental concepts about resilience of broadband infrastructure in disasters that public sector leaders should understand. Those concepts include the following:
- Different disasters require different mitigation strategies during construction of networks. Mitigation efforts need to be tailored to the specific risks — even down to the census block, street, or individual parcel of land — to be most effective.
- Power resiliency and broadband resiliency are linked. Power outages can render otherwise undamaged broadband networks unusable, and public sector officials facilitating broadband deployments need to understand network vulnerabilities related to damaged power supply, insufficient backup power at critical network equipment, and the role of in-home backup power.
- Some disaster mitigation strategies are expensive, and there will always be tension between building expensive but more resilient networks, and building cheaper but less resilient ones. However, ensuring at a minimum that widely accepted construction best practices are followed (which is not a guarantee when networks are being built quickly with insufficient staff), paying closer attention to networks utilized by public safety, encouraging extra resiliency measures for networks that feed critical mobile broadband deployments, and networks located in at-risk areas, can help improve the overall resilience during and after disasters.
The research methodologies created for this report also informed the creation of the Broadband Climate Risk Mitigation Tool, an interactive resource to support public sector officials of all levels and prospective BEAD subgrantees in understanding disaster resilience and broadband vulnerabilities down to the census block level.
Recommendations
Our recommendations for use of the tool by various stakeholders include the following:
- State broadband offices: State broadband offices need to analyze the specific contexts of broadband deployment proposals to ensure these deployments mitigate disaster risk. Using the Broadband Climate Risk Mitigation Tool, state offices can:
- Better evaluate deployment plans, and ask questions of applicants to ensure their networks are going to meet the needs of specific communities during disasters
- Prioritize field and compliance checks of funded infrastructure in disaster-prone areas to ensure construction best practices are being followed in the most critical areas
- Local government: Officials in local government organizations can use the tool to have informed conversations with potential ISP partners deploying broadband infrastructure in their jurisdictions. For example, local officials can use the tool to:
- Evaluate deployment plans, and potentially predicate support of a BEAD applicant in part by sufficiently communicating a plan for resilience in high-risk areas
- Understand where networks used with public safety applications may intersect with vulnerable areas, and request appropriate additional resiliency measures
- BEAD subgrantee applicants: BEAD applicants can use the Broadband Climate Risk Mitigation Tool to understand census-block-level vulnerabilities in planned broadband deployments. This may inform:
- Site selection of critical electronic components such as central offices, hubs and generators
- Locations of redundant fiber routes, or even alternate modes of construction in critical areas (e.g., buried rather than aerial)
There are many structural barriers to taking climate and disaster resiliency into full account when deploying broadband. Even beyond the inherent tension between the expense of resilient networks and the imperative to build as many miles of fiber as we can, it is often the case that FEMA will pay for infrastructure repair in the event of major disasters, which, in many instances, reduces the incentive for ISPs to spend significantly more to build more disaster-proof networks in the first place.
However, it is our hope that public sector officials and sub applicants alike can use this report and the Broadband Climate Risk Mitigation Tool to make more informed decisions related to disaster resilience, prioritize resilience wherever possible, and thereby save time, money, and potentially lives in disaster recovery in the decades to come.
Understanding broadband resilience and natural disaster risk
The stability of a broadband network, especially during crucial connectivity periods, depends on its resilience. Recognizing that resilience differs greatly across regions helps stakeholders fortify vulnerable communities more effectively against harmful weather events in the future.
What is broadband resilience?
A resilient broadband system can withstand damages and minimize the likelihood of service outages. Typically, a resilient system requires:
- Route diversity: The availability of multiple paths without common points
- Redundancy: The provision of duplicate assets to provide backup
- Protective measures: The additional processes and systems used to reduce the likelihood that a system will be affected by natural disaster
- Restorative measures: The additional processes and systems used to reduce the time needed to return a system to full functionality
While it is preferable to incorporate resilience in the initial design stage, resilience can also be incorporated in the maintenance stage by retrofitting existing infrastructure or in emergency planning for network failures. (Cybersecurity and Infrastructure Security Agency, 2018).
What are the effects of disasters on broadband resilience?
Disaster-related consequences can impact broadband equipment in several ways, including shortening lifespan (see table below for estimated useful life of telecom infrastructure), impacting service quality, and causing failures.
- Flooding: Flooding caused by heavy rainstorms, hurricanes, and coastal and riverine flooding poses a great risk to broadband equipment, especially ground-mounted equipment like network hubs and central offices. Utility poles or even buried fiber can be impacted as well due to saturated ground, river wash-outs, or even corrosion due to prolonged exposure.
- Wildfires: In addition to direct fire damage, wildfires can lead to electrical surges, electrical short circuits, and equipment damage to aerial, buried, and wireless equipment. Wildfires can melt communication lines as well as electric lines, leading to telecommunication outages.
- Winter storms: Ice storms and snowstorms can cause heavy ice buildup on overhead lines and other equipment or on nearby trees, potentially leading to structural failure due to lines breaking or branches falling into lines.
- Heat waves: Heat waves can lead to equipment failure and higher energy costs, though most often heat waves cause power blackouts due to extra draw on the energy grid that then impacts broadband.
- Wind, tornadoes, and hurricanes: Wind storms, hurricanes, and tornadoes can cause direct damage to all exposed equipment, such as utility poles, cables, ground-mounted equipment, and wireless infrastructure. These events are often associated with significant rain and storm surge and so can bring flooding as well.
- Earthquakes: Significant earthquakes can cause structural stress or failure in many types of broadband equipment, including aerial and buried infrastructure, especially near fault lines, and other sensitive equipment such as landing stations.
How do regions compare from a resiliency standpoint?
Not all regions face the same broadband resiliency challenges. Resilience can vary widely based on the specific disaster risk that each region faces, as well as the strength or resilience of the region’s current telecom equipment. An evaluation of a region’s specific broadband resilience against relevant disasters can help vulnerable regions more effectively prepare themselves against adverse weather events.
To show regional differences, our analysis used FEMA’s expected annual building losses (EABL) to represent relative risk profiles, where the higher the building loss value, the higher the risk for climate disaster. FEMA’s data is made available at both the census tract and county level.
However, we used census tracts, which are different from census blocks, for the purposes of this report. To assemble the risk profile ratings, we applied the methods used by FEMA to calculate relative risk profiles for all census blocks that had a risk of disaster greater than zero. The risk profiles and rating system are as follows:
- Hazard risk scores: Scores represent the national percentile ranking of the community’s expected annual losses compared to all other communities at the same level (county or census tract) where expected annual building losses are greater than zero .
- Hazard ratings: Ratings are provided in one of five qualitative categories describing the geographic area’s EABL values in comparison to all other communities at the same level. Rating categories range from “Very Low” to “Very High.”
From there, we applied the following classifications used by FEMA to classify the hazard ratings.
- Very High: 80th to 100th percentiles
- Relatively High: 60th to 80th percentiles
- Relatively Moderate: 40th to 60th percentiles
- Relatively Low: 20th to 40th percentiles
- Very Low: 0th to 20th percentiles
With these parameters we analyzed vulnerabilities in unserved census blocks at a statewide and regional level to understand the prevalence of potential risk.
The analysis found that hurricanes and earthquakes cause the most destruction across the U.S., accounting for about 68% of all EABL. Hurricanes and earthquakes are followed by riverine flooding, tornadoes, and wildfires, which together account for about 23% of all losses. (Earthquakes, while rare, have the potential to cause significant widespread destruction, and so rank high in this expected annual loss calculation.)
Riverine flooding — while likely causing less loss than hurricanes and earthquakes — is more widespread, being a top-three loss-causing hazard in as many as 35 U.S. states.
The most “high risk” (approx. 138,000 census blocks) and Relatively Moderate risk unserved areas (approx. 208,000 census blocks) fall in the South. When we refer to “high risk” areas, we are including areas FEMA has designated as Very High and Relatively High risk.
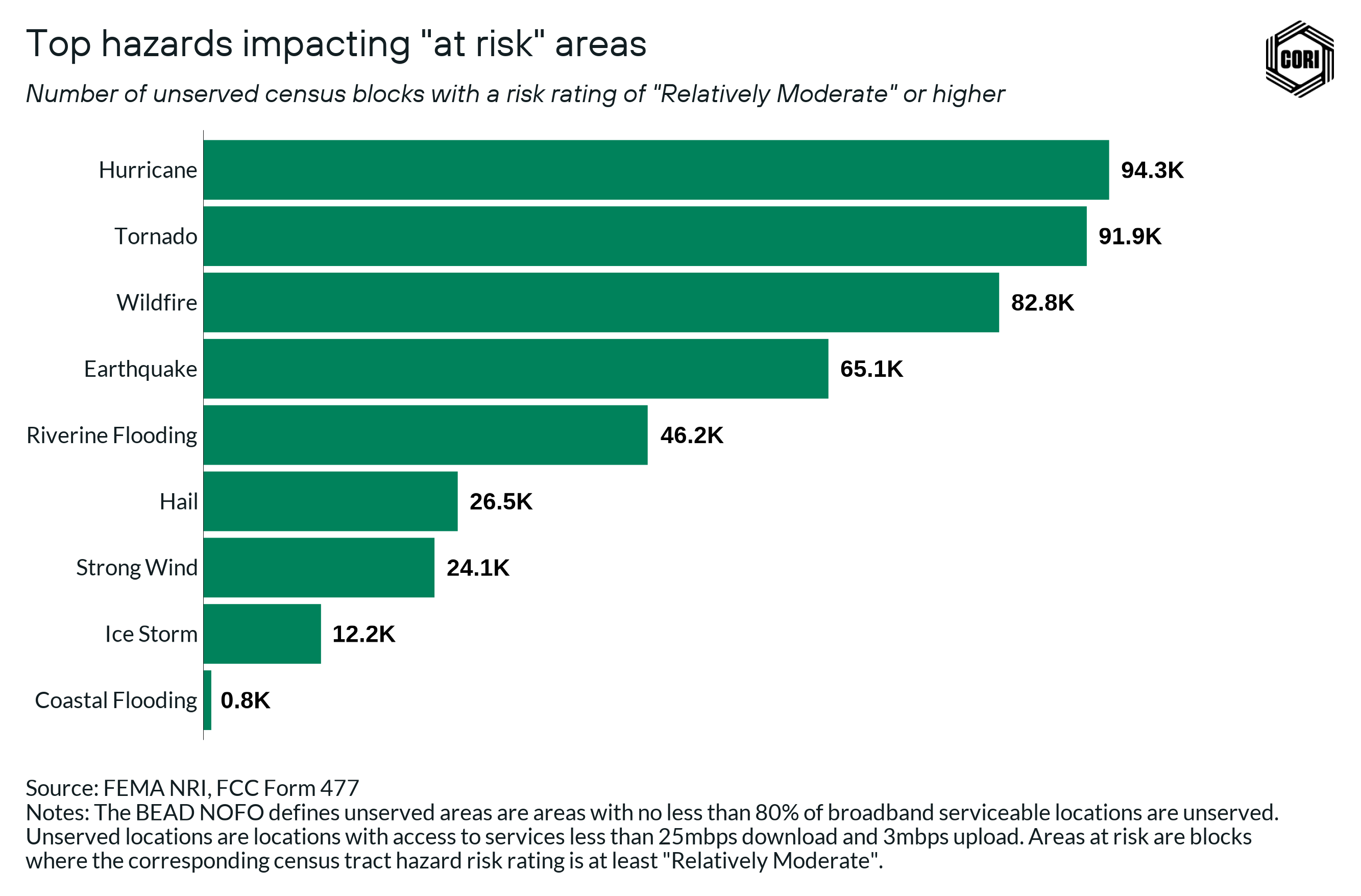
The figure below shows that more than 80,000 unserved areas are rated Relatively Moderate risk or higher for hurricanes, tornados, and wildfires.
In the analysis above, we use unserved census blocks that are likely to be broadband investment priorities going forward and experience average to above average climate risk to identify the top hazards to be considered when building broadband infrastructure. We still see that hurricanes remain the top concern even at the localized level, with wildfires emerging as an increased concern due to wildfires impacting a significant portion of rural areas in the West.
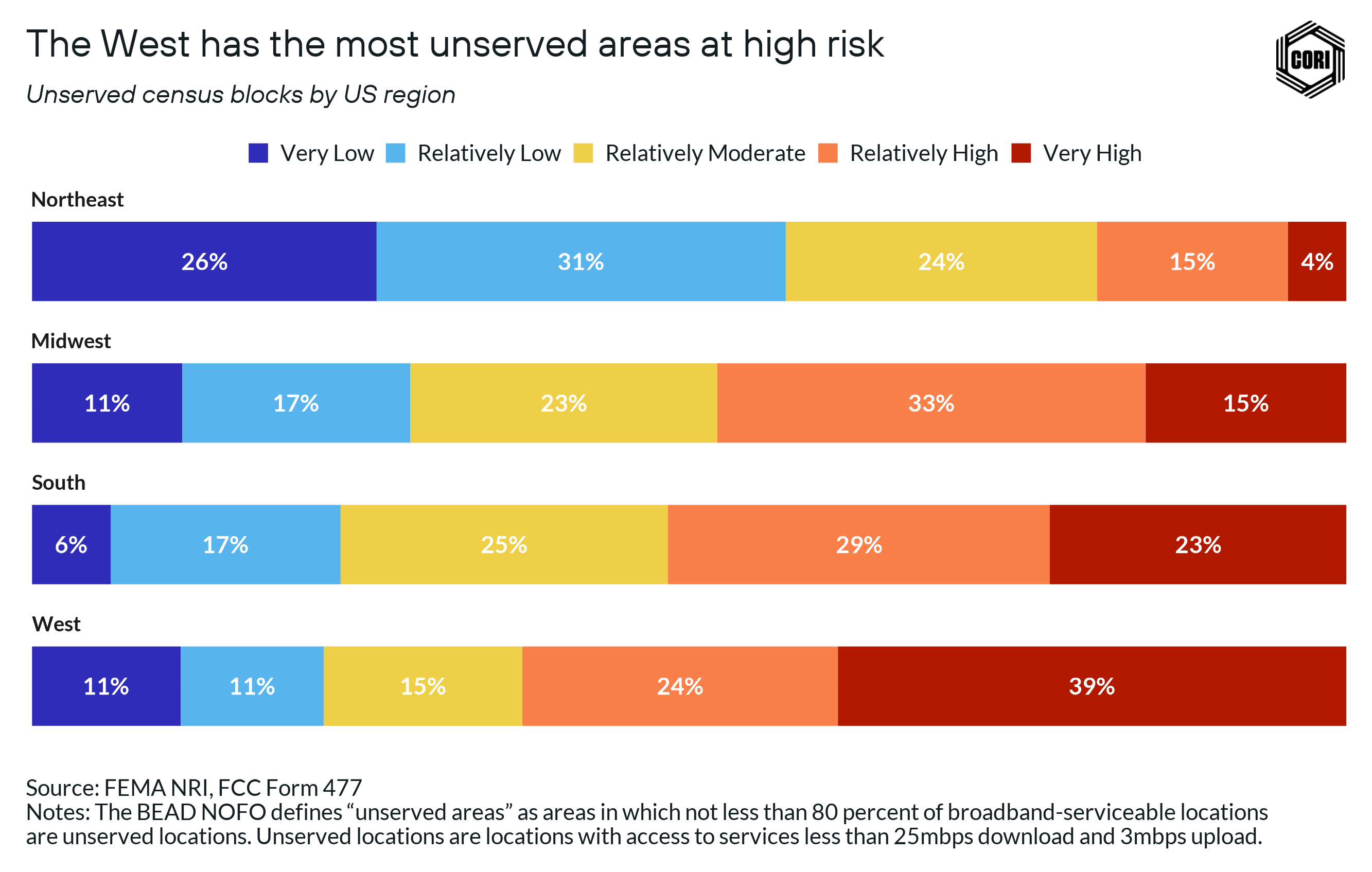
In terms of percentage, the West region has the most areas at high risk (62%) and at least Relatively Moderate risk (78%). Apart from the South and West, the Midwest region also has a large number of high risk (47%) and at least Relatively Moderate risk (71%) areas.
A significant proportion of unserved areas — 47% and above — in all regions, except the Northeast, are at high risk where BEAD investments can be helpful. But even in the Northeast, 42% of unserved areas face at least Relatively Moderate risk challenges.
To better understand the intersection between climate risk, broadband investment areas (census blocks that are defined as unserved or underserved in the BEAD Notice of Funding Opportunity), and social vulnerability and community capacity, we identify areas that are disproportionately impacted by poverty, unemployment, and low per capita income. The private ISP market is less likely to invest resources in these areas, ultimately leaving these areas out of infrastructure development plans. BEAD investment in these areas is vital to eliminating the existing infrastructure gaps.
To identify these areas of high need that are more likely to require outside investment, we use the Index of Deep Disadvantage (isolating counties that are classified as either Disadvantaged or Most Disadvantaged), the Economic Development Agency’s (EDA) distress criteria, and the U.S. Census Bureau’s data on persistent poverty counties. If unserved areas meet any of these criteria, we’ve categorized them as socially vulnerable.
The most vulnerable populations that lack key broadband infrastructure are found in hurricane-prone areas, however, vulnerable populations without broadband are found across the U.S. to one degree or another. These populations are where BEAD funding is most needed to develop resilient broadband infrastructure.
Given the overlapping challenges that socially vulnerable populations face in getting connected beyond infrastructure access — device access, affordability, etc. — and the heightened risk to housing and personal safety in disasters (i.e., the prevalence of manufactured homes in flood plains, and regions prone to tornadoes and hurricanes), it is critical that these regions are not provided with infrastructure at inordinate risk of failing during disasters when communication and public safety functions are essential to saving lives.
Broadband network vulnerabilities
Different disasters require different mitigation strategies during construction of networks to reduce risk and increase resiliency. Mitigation efforts need to be tailored to the specific risks present in specific areas — which can change from one side of town to another, and even from street to street.
The truth is, almost no type of infrastructure is fully immune to natural disasters — and certainly not to human-error disruptions like a car crashing into a telephone pole or a tractor digging up a buried cable.
However, increased education amongst public sector officials at all levels on risks and mitigation strategies will contribute to better decision-making around when to encourage or insist on investments in more resiliency measures.
This report includes a detailed appendix (see Appendix A) documenting the specific risks to aerial and underground wireline infrastructure, as well as wireless infrastructure, due to specific disasters. The appendix also includes a list of the possible mitigation efforts for each type of infrastructure that can help increase resilience to disasters.
Importantly, power resiliency and broadband resiliency are linked, and the co-occurring challenges of telecommunications and power disruption during disasters is well documented. In terms of weather events, windstorms and hurricanes are the dominant cause of power failures, although power failures can also be caused by thunderstorms, ice storms, and other winter winter events (Jacob et.al., 2011).
Over time, the frequency of electric-grid disruptions caused by extreme weather has increased, in turn leading to an even greater number of telecom outages (Rosenzweig et.al., 2011). While broadband infrastructure increasingly relies on energy grids and already accounts for a substantial amount of today’s energy consumption, this dependency is increasing with the introduction of advanced technology (Adams et al., 2014).
The power challenge becomes exacerbated in remote, rural areas with less consumer reporting and equipment maintenance (Adams et al., 2014). These customers have fewer backup service options, and sometimes lack wireless and broadband services. Service restoration following a storm often takes place much later in rural areas, with smaller, remote communities likely to be restored last, placing them at increased risk during emergencies (Rosenzweig et al., 2011).
Case studies on broadband resilience
The following case studies from past disasters in the U.S. underscore the need for strengthening broadband resilience in isolated areas, the interconnectedness of power outages and telecom disruptions, and the significance of adhering to top-notch resilience practices. These case studies also offer real examples of how to better build resilience into broadband infrastructure.
Case Study 1: The 2017 Atlantic hurricane season
Remote location, power outages, and disregard of resiliency practices causes major broadband damage in Puerto Rico and the U.S. Virgin Islands
Overview
With over $200 billion in damages and several lives lost, 2017 was the most expensive hurricane season in U.S. history. The season started in August when Hurricane Harvey caused over 100 deaths in the Houston, Texas, area.
This was followed in September by Hurricane Irma, which affected the U.S. Virgin Islands (USVI), Puerto Rico, and some areas in Florida. Hurricane Maria followed, largely affecting Puerto Rico and the USVI, and causing immense damage. October led to Hurricane Nate arriving and causing flood damage in the north Gulf Coast region (Mississippi to Florida) (Federal Communications Commission, 2018).
Challenges
- Power outages: Puerto Rico took 11 months to restore power to all its citizens after Hurricanes Irma and Maria, which is the longest blackout in U.S. history (Zahn, 2022).
- Telecom outages: Hurricane Irma and Maria severely damaged broadband infrastructure in Puerto Rico and the USVI.
- Hurricane Irma caused over half of the cell sites in the USVI to be out of service, and Hurricane Maria led to 95.2% of cell sites in Puerto Rico and 76.6% in USVI to be out of service (Federal Communications Commission, 2018).
- Around 80% of aboveground fiber and about 90% of last-mile fiber was completely destroyed in these disasters in Puerto Rico and USVI. (Sandhu & Raja, 2019).
- The Puerto Rico and USVI call centers suffered significant damages, causing them to be mostly out of service (Federal Communications Commission, 2018).
- Remote location: Puerto Rico and the USVI are located about 1,000 nautical miles from the U.S. mainland, making it extremely difficult to access the personnel, equipment, and resources needed to support disaster response and recovery (Government Accountability Office, 2021). With Hurricane Maria, it took as many as six months for wireless services to be restored, with portions of cell sites still out of service even after this time period. Cable systems and wireline phone services remained generally nonexistent, mostly due to the lack of power. Even months after the disaster, the USVI did not have working television broadcasting, cable systems, and wireline services (Federal Communications Commission, 2018).
Resiliency strategies
- Public agencies: The FCC created an internal incident management team, activated the Disaster Information Reporting System (DIRS), eased regulatory requirements for providers, and provided about $77 million to eligible carriers for restoration efforts in Puerto Rico and the USVI (Federal Communications Commission, 2018).
- Private operators: Private operators provided fuel topping in backup generators at cell sites, refueling trucks, portable cell towers, temporary microwave links to replace broken fiber links, drones to assess cell tower damage, and small-cell technology that reduces the cell site’s size and makes the networks more resilient (Reardon, 2017).
Lessons learned
- Ensure resiliency in remote areas: A critical learning that emerged was to ensure service providers create more resilient broadband infrastructure in remote/geographically isolated areas, such as islands, mountainous, and rural areas. Quick disaster recovery was difficult due to the distance from the mainland. Storm damage to airports and seaports also did not help in the response efforts (Government Accountability Office, 2021). There is a critical need today to build greater infrastructure resilience and also generate more awareness of the challenges being faced in rural and remote areas.
- Adopt best practices: Several best practices should have been followed in this situation, including undertaking periodic site structural audits of telecom towers; increasing physical path diversity before (via redundant fiber routes) and after disasters , such as usage of satellite networks, microwave links, or alternate wireline connections; using higher-ground areas (above the predicted storm-surge levels) for placing all power and network equipment to increase reliability; ensuring emergency/backup power (e.g., batteries, generators, fuel cells), and upgrading existing Land Mobile Radio Systems.
- Use emerging tech/alternative communication methods: New technologies such as cell sites on wheels (COWs), temporary microwave links drones, and small-cell technology were used to help in restoration. Apart from traditional communication methods, users also availed of alternate communication methods, such as amateur radio and satellite phones, especially in Puerto Rico and the USVI (Federal Communications Commission, 2018).
Case Study 2: California wildfires
Power outages lead to telecom disruptions making rural populations vulnerable.
Overview
Frequent wildfires have had devastating consequences, particularly in the western U.S., but increasingly in other areas of the country as well.
In fall 2019, California faced a major fire due to a likely power line spark, which, when combined with low humidity and strong Santa Ana winds, destroyed hundreds of dwellings and caused approximately 100,000 people to flee (AP News, 2020). Starting Oct. 23, 2019, the Kincade Fire burned through 77,000 acres north of the San Francisco Bay Area, while the Getty Fire burned through 745 acres outside Los Angeles, all in the course of a few weeks (Anderson et al., 2020).
Challenges
- Power outages: According to the California Department of Forestry and Fire Protection, power lines northeast of Geyserville were responsible for starting the Kincade Fire (AP News, 2020). In order to reduce further damages, power utilities switched off electricity in the area, affecting millions of people (AP News, 2019). While power could have been restored fairly quickly, tower repair and rolling blackouts to limit the fire’s spread prevented this from happening (Anderson et al., 2020).
- Telecom outages: From Oct. 25 to Nov. 1, 2019, there were as many as 874 cell sites out of service, some for the entire eight-day period. The major cause of the cellular issues was loss of electricity, affecting 80% of the towers, with backhaul issues and equipment destruction leading to the other 20% of issues (Feld, 2019). The power outage also affected more than 390,000 cable and wireline subscribers (Federal Communications Commission, 2018).
- Remote locations: An important counter-measure in such disasters is local authorities sending evacuation warnings to residents. However, as landlines collapsed, the power outage increased the risk for rural community residents without cell phone or internet service. Such residents would have been unable to receive any evacuation warnings had the fire spread further (Miller, 2019). In a related incident, a 2020 “Lightning Complex Fire” in California also brought out another challenge: Residents waiting for an evacuation message never received it because the messages were part of an “opt-in” service. Residents living around county boundaries also did not receive such messages due to their intermediate location (Deale, 2020).
Resiliency strategies
- Public agencies: The FCC asked the private operators on Sept. 15, 2019, to provide their contingency plans due to the upcoming disaster and planned power outage. After the 2018 wildfires, service companies were informed that California power companies may engage in future extended “power downs” to reduce the risk of wildfires (Feld, 2019). FCC also activated the Disaster Information Reporting System (DIRS) in 37 California counties to monitor telecom infrastructure (Anderson et al., 2020).
- Private operators: Some private operators installed backup generators and batteries to reduce telecom outage. For example, Verizon deployed generators and backup batteries at most cell sites and all of its switch locations. Prior to the Kincade Fire, AT&T deployed additional crew from around the country to refuel and deploy generators. The company also helped its customers by waiving charges and providing credits for unlimited talk, text, and data access (Miller, 2019).
Lessons learned
- Combat power outages: Future wildfires will continue to cause power shutdowns in California and other states. To combat power outages, service providers need to ensure multiple-day backup generation plans, such as using a combination of solar cells and battery storage. Providers also need to work with power utility companies to implement the best defensive methods to ensure power, especially at cell sites (Anderson et al., 2020). Some positive efforts in this direction are being made. For example, AT&T, which has invested over $650 million in its Network Disaster Recovery (NDR) program, is already looking at an upgrade of its flying COWs system with 5G antennas, which can recreate a cellular network.
- Adopt best practices: Cell sites need regular maintenance, including curbing vegetation growth around them to help prevent damage during wildfires. Using nonflammable building materials or fire-retardant coatings for towers can help reduce damage as well. Routing distribution networks around roadways or railways, which are subject to consistent vegetation management, can also help, as can leveraging non-flammable areas such as large fields/parking lots to act as fire buffers (Anderson et al., 2020).
- Prepare for the future: Cellular networks are one of the most important emergency communication channels in natural disasters. Eighty percent of all 911 California wildfire emergency calls were made through cell phones (Anderson et al., 2020). Rural areas without access to cell phones or with out-of-service cell sites can be a major challenge for authorities when communicating for a safe evacuation.
Case Study 3: Hurricane Sandy (2012)
Power outages and flooding cause significant damage in New York.
Overview
Hurricane Sandy made landfall on the east coast of the U.S. on Oct. 29, 2012. The storm was one of the most devastating in New York’s history, causing 43 deaths and around $19 billion in damage. This massive storm led to a 14-foot storm surge or “storm tide,” which flooded 51 square miles (17%) of New York City’s total land mass. Most of the deaths reported in the disaster were due to this flooding (New York City Government, n.d.).
Challenges
- Power outage: Over 8.5 million residents were affected by power outages, which also affected telecom services such as phone, wireless, cable, and internet. It took 13 days to restore power in most areas, cut down approximately 41,000 trees, replace 2,500 poles, install 1,000 new transformers, and clean all flooded substations (Penn Live, 2012).
- Telecom outage: Over 1 million cellular customers in New York City were without service when cell site backup batteries ran out hours after the electric grid went down. (New York City Government, n.d.). Where the network was available, high volumes of call traffic led to network congestion and service interruptions.
- Twenty-five percent of all cell sites and cable services in 10 states, the majority in New York and New Jersey, were affected. For example, all cell sites in Long Beach, N.Y., serving over 35,000 residents, were knocked out by the storm (Reardon, 2017).
- Inland flooding damaged power backup equipment, including onsite diesel generators and fuel pumps in many facilities. This disrupted landline and internet service for up to 11 days in some inland areas. Coastal area flood damage to telecommunications equipment and cabling caused even longer outages, with saltwater damaging a significant number of cable vaults and structures. Water and high winds also brought down overhead lines across residential sections, causing further disruptions (New York City Government, n.d.).
- Slow restoration: Post flooding, restoration was quicker for service providers with modern networks and more resilient infrastructure. In certain Lower Manhattan buildings, Verizon started replacing corroded copper cables with fiber to ramp up resilience. However, the majority of the buildings did not have service restored fully even after 60 days (New York City Government, n.d.).
Resiliency strategies
- Public agencies: The FCC initiated the DIRS and also worked in its restoration efforts to support FEMA’s work. The FCC chairman mentioned many telecom failures due to “the interrelation of our electric grid and our communications networks” (Reardon, 2013). The New York City mayor’s office worked with many government agencies and service providers to deploy COWs, COLTs, and charging stations near central distribution sites and community centers to ensure connectivity (Gibbs & Holloway, 2013).
- Private operators: Verizon deployed Wireless Emergency Communications Centers (WECC) or trailers, which had computer workstations, wireless phones, and charging ports stationed for customers. AT&T provided charging stations or trailers at major food and water stations in all the five boroughs of the city. Both companies also offered free charging facilities at their stores (Stern, 2012).
Lessons learned
- Prioritize combating power outages: The relationship between power and telecom outages was again confirmed, as was the value of having enough backup-power options at cell sites.
- Adopt best practices: The advantage of sturdier fiber networks as opposed to copper cables was easily visible in this storm. Another best practice was locating the central offices and equipment in elevated areas — both off the ground and on higher floors when possible. Quicker post restoration for sturdier networks and the ability for providers to proactively modernize their networks was also a major learning.
- Use Emergency Tech: Although cellular communication was hit with considerable outages, the usage of COWs, COLTs, and charging stations or trailers were all helpful restoration aids. Enabling text messaging helped with quick communications among users, lessening the need for lengthy phone conversations that would have congested the network even more (Reaedon, 2012).
Recommendations for public sector leaders and broadband builders
Increasing the resilience of our broadband and telecommunications networks is of vital importance, but is also a challenging endeavor that requires balancing conflicting priorities in the funding and policy realms.
These recommendations are meant to be measured, concrete steps, informed by data and research, that various stakeholders involved in the BEAD process and future broadband deployments can take.
State broadband offices
Above all else, state broadband leaders need to understand best practices for building resilient telecommunications networks and be explicit about the best practices for construction that all BEAD subgrantee recipients must adhere to.
In addition to construction practices, state offices can encourage resilient design, such as the incorporation of redundant routes through low-risk areas, the inclusion of sufficient extra strands and capacity to accommodate population growth and potential additional use by mobile broadband providers and emergency communications systems.
If applications include deployments in high-risk areas, which can be evaluated using the Broadband Climate Risk Mitigation Tool, states may ask that applicants preemptively list resiliency measures the plan is taking, and evaluate the strength of those measures based on the risk of the locations. The locations of central offices and network hubs are especially important to place with care and states should encourage BEAD subgrantee applicants to refer to risk maps when placing this critical equipment.
States may also prioritize field and compliance checks of funded infrastructure in disaster-prone areas to ensure construction best practices are being followed in the most critical areas. Given the common usage of contractors, subcontractors, and even sub-subcontractors in the broadband deployment space, there is a critical compliance role for public officials to play to verify that promises made in BEAD applications are met in practice.
A coordinated effort between state and local officials may be useful on this front — by equipping local leaders with information on resiliency and construction best practices, they can act as on-the-ground support in verifying and encouraging broadband builders to adhere to appropriate standards.
Local government
Officials in local government organizations can use the tool to have informed conversations with potential ISP partners deploying broadband infrastructure in their jurisdictions. Regardless of whether the partnership is complex and robust, or simple and straightforward, local public sector leaders should feel empowered to encourage and insist on appropriate resilience measures. Even just asking what measures are being taken from an informed position will signal to potential partners a sophistication and attentiveness to this issue.
A common aspect to ISP partnerships is an explicit usage of new deployments for municipal functions and public safety services. Local governments need to understand when networks used with public safety applications intersect with vulnerable areas, and may request appropriate additional resiliency measures.
Lastly, knowing how to recognize that care is being taken during construction is another essential role for local officials to play. If contractors are leaving construction trash, sloppy slack loops, or even not repairing lawns properly, this can be a sign that hasty work is being performed and may make networks less resilient. Local public sector officials should feel empowered to talk with company representatives about the importance of following construction best practices in vulnerable areas and across their jurisdiction as a whole.
BEAD subgrantee applicants
BEAD subgrantee applicants — in other words, entities who will be building broadband networks — can use the Broadband Climate Risk Mitigation Tool to understand census-block-level vulnerabilities in planned broadband deployments. The tool may be particularly useful in site selection for critical network components such as central offices, network hubs, and generators.
Lastly, BEAD subgrantee applicants can use FEMA data and risk assessments to inform other aspects of network construction, such as the pathways of redundant routes, and even locations where underground construction may be preferable to aerial.
Acknowledgements and resources
This project would not have been possible without funding and support from Connect Humanity, as well as the valuable insight and expertise of Andrew Afflerbach at CTC Technology & Energy, and the research work of Devin Fidler, Rajeev Mehta, and others. CORI would like to thank them for their contributions to this effort.